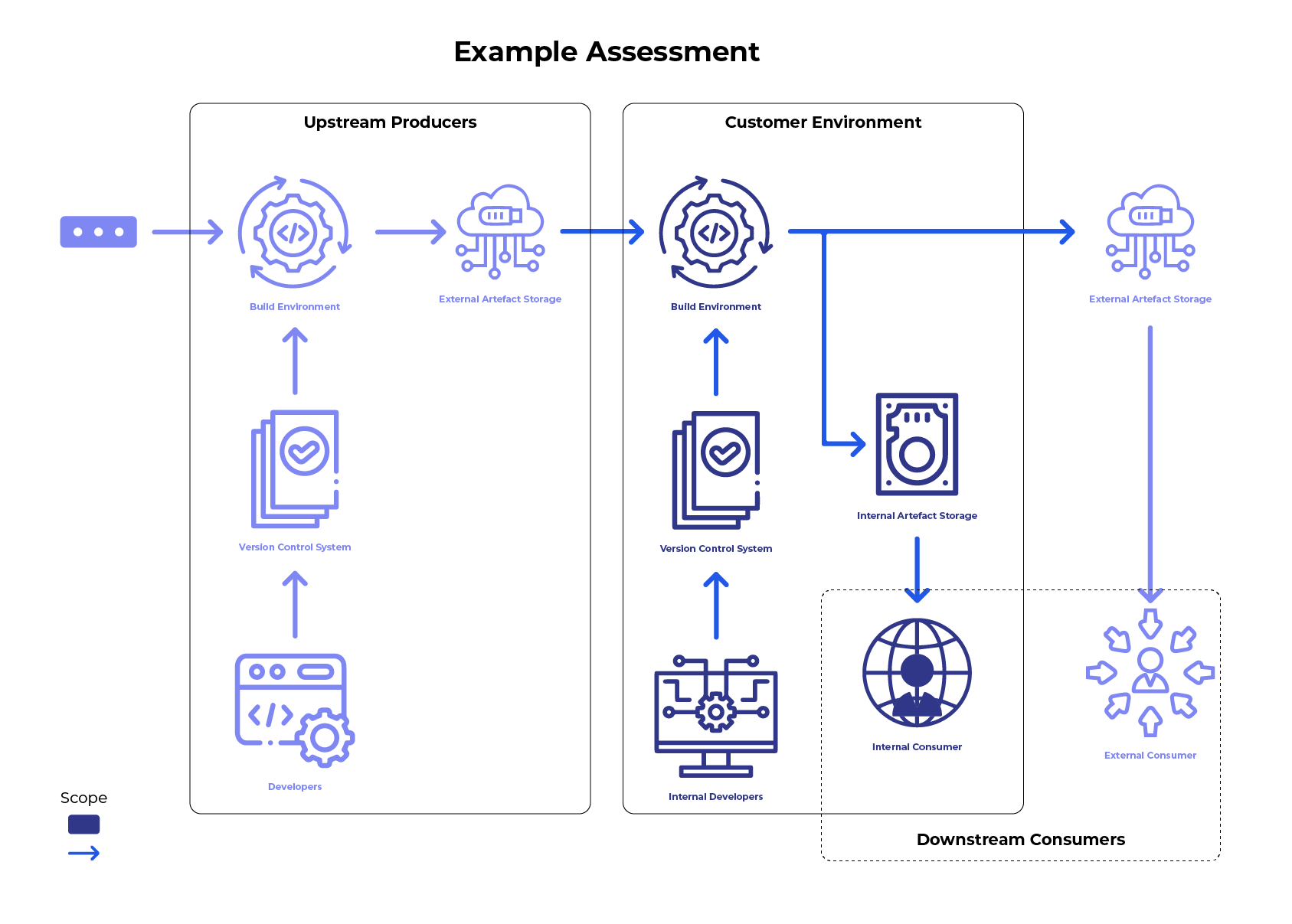
Our Software Supply Chain Security Assessment identifies security risks in your organisation’s Software Supply Chain.
We work with you to explore your development security: from the moment dependencies enter your organisation, through secure build and packaging, to the final artefacts being deployed or distributed.
You will receive a report detailing which aspects of your Software Supply Chain pose the most significant risks to your organisation and what actions you can perform to mitigate these. Additionally, engineering teams will gain valuable insights into best practices you can implement for building and distributing your software artefacts thereby increasing user trust in your products and services.
What do you get?
Deliverables included in the default offering:
- Executive summary
- Categorised findings
- Actionable recommendations
- Risk review
- Roadmap
Further deliverables that can be added include:
- Attack trees
- In-depth remediations advice
- Controls mapping
- Maturity Assessment
- Maturity Level report
- Strategic workstream proposals
Who’s it for?
Organisations that are consumers and/or producers of software artefacts (containers, binaries, source code etc) and are looking to:
How is this delivered?
The Supply Chain Security Assessment includes:
- Direct access to a team of experienced professionals who can tailor the assessment to the organisation’s unique needs and requirements
- A fresh assessment that is not based on a standard template or output, providing a more comprehensive and personalised evaluation of the security posture of the organisation’s Software Supply Chain
What’s next?
Following on from the findings, we can: